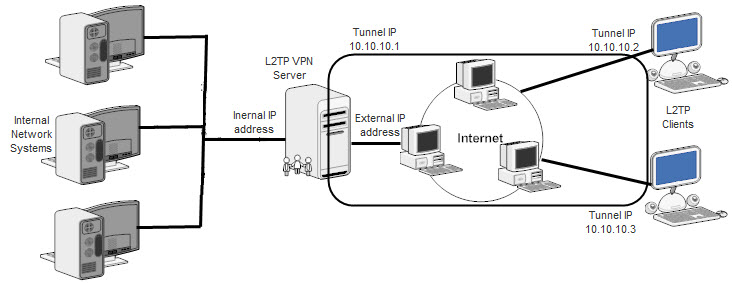
L2TP (Layer 2 Tunneling Protocol) is a tunneling protocol used for VPNs. It uses the UDP port 1701 to communicate. It doesn’t have any encryption, but we can encrypt the L2TP packets by using it with IPSec. For theoretical information on L2TP you can visit its Wiki.
In Linux, you can find so many different applications to build a L2TP server but there is no proper documentation for this. Also, I think no one is using L2TP VPN nowadays. But my requirement could solve by L2TP only. I wanted to configure the VPN for some old devices that does support only L2TP VPN.
I use Centos 5 Linux for VPN server. For VPN application, I use the combination to two applications. One is xl2tpd & rp-l2tpd.
I also had the option of openl2tpd, I tried this on Fedora 8 Linux but there is some bug on fedora 8’s pppd, which stopped me to use that. And when I tried to install openl2tpd on Centos 5, it asked to enable the L2TP support on kernel. I didn’t want to play with kernel that time.
That was the reason, I switched to xl2tpd application. It is the same application l2tpd but maintained by Xelerance Corporation. I don’t use l2tpd due to some compilation problem. I also face the compilation problem with xl2tpd, but it was manageable. You will also see the use of rp-l2tpd, it is also solving some dependency problem for xl2tpd.
Downloading & Installing xl2tpd
xl2tpd can be downloaded from http://www.xelerance.com/software/xl2tpd/xl2tpd-1.2.4.tar.gz or you can download it from any other website. After downloading the application use the following commands to install it.
| root@rahul-pc~# tar –xvf xl2tpd-1.2.4.tar.gzroot@rahul-pc~# cd xl2tpd-1.2.4 root@rahul-pc~# make |
When you give the make command, it can show you some error on compilation (especially on fresh installed Centos 5 system, may be due to some dependencies), but creates the xl2tpd binary. You can use that binary for configuring L2TP VPN server. Copy that binary to /usr/local/sbin/ directory.
| root@rahul-pc~# cp xl2tpd /usr/local/sbin/ |
xl2tpd.conf
Also copy the xl2tpd.conf file, from the examples directory on your xl2tpd source directory, to /etc/xl2tpd/ directory (you need to create that directory as you installing the xl2tpd manually).
| root@rahul-pc~# cp examples/xl2tpd.conf /etc/xl2tpd/ |
Change the xl2tpd.conf according to your usage; means change the IP address in conf file that you require for your VPN network i.e. tunnel IP address. In my case xl2tpd.conf file look something like this.
| ;; This is a minimal sample xl2tpd configuration file for L2TP without IPsec. ; ; The idea is to provide an L2TP daemon to which remote L2TP clients can ; connect. In this example, the internal (protected) network ; is 192.168.1.0/24. A special IP range within this network is reserved ; for the remote clients: 10.10.10.0/24 ; (i.e. 10.10.10.1 ... 10.10.10.254) ; ; The listen-addr parameter can be used if you want to bind the L2TP daemon ; to a specific IP address instead of to all interfaces. For instance, ; you can bind it to the interface of the internal LAN (e.g. 192.168.1.98 ; in the example below). [global] ; listen-addr = 192.168.1.98 ; ; requires openswan-2.5.18 or higher - Also does not yet work in combination ; with kernel mode l2tp as present in linux 2.6.23+ ; ipsec saref = yes ; forceuserspace = yes ; ; debug tunnel = yes ; L2TP Network Server configuration. [lns default] ip range = 10.10.10.2-10.10.10.254 local ip = 10.10.10.1 ; Always use CHAP instead of PAP, it will provide you a little security ; with L2TP (without IPsec). require chap = yes refuse pap = yes require authentication = yes name = LinuxVPNserver ppp debug = yes ; PPP option file name, it may use /etc/ppp/options by default, if you comment this pppoptfile = /etc/ppp/options.xl2tpd length bit = yes |
You can modify this file according to your requirement. The entire configuration is completed from xl2tp side, now time to configure the PPP parameters.
options.xl2tpd
First of all, create a file named /etc/ppp/options.xl2tpd (option file name written in xl2tpd.conf file) with following entries.
| ipcp-accept-localipcp-accept-remote ms-dns 192.168.22.240 ms-wins 192.168.22.240 noccp auth crtscts idle 1800 mtu 1410 mru 1410 defaultroute debug lock proxyarp connect-delay 5000 |
You can change your dns & wins server IP address in the file. You can also add some other parameters that are supported by your pppd, like require-mschap-v2, see the man page of your pppd.
chap-secrets
Put your authentication on /etc/ppp/chap-secrets file.
| # Secrets for authentication using CHAP# client server secret IP addresses "username" "*" "password" "10.10.10.2" |
The IP address field is showing the remote tunnel static IP address. You can assign the dynamic IP addresses also by using radius server & dhcp-pppd plugin etc. But I don’t know what is the easiest method to do this & how to. Also my requirement is completed by using static IP address. But I want to know its other methods also. Anyone, who can put some light on this, please writes.
Same chap-secrets file can be used, if you are using mschap protocol in option file.
Running xl2tpd
After doing the entire above configuration, you can start xl2tpd. Give the following command.
| xl2tpd -D |
-D option is opening the debug of xl2tpd. It is recommended to start the application in debugging mode at first time (during testing time). Remove –D option to stop the debugs.
When you try to run xl2tpd, it will show you a error for /var/run/xl2tpd/l2tp-control not found. This l2tp-control file can be extracted from rp-l2tpd application. Or you can compile the xl2tpd properly, may be it will gives you the l2tp-control binary. You can also try this by creating a blank non-binary file by using touch command (I didn’t try this, it’s just a silly ideaJ).
Download & compile rp-l2tpd to get the l2tp-control
To download the rp-l2tpd go to http://sourceforge.net/projects/rp-l2tp/. Compile the application by following commands.
| root@rahul-pc~# tar -xvf rp-l2tpd-0.4.tar.gzroot@rahul-pc~# cd rp-l2tpd-0.4 root@rahul-pc~# ./configure root@rahul-pc~# make |
After successful compilation you can copy the l2tp-control binary to /usr/local/sbin/ directory.
| root@rahul-pc~# cp handlers/l2tp-control /usr/local/sbin/ |
Create the soft-link of control file to /var/run/xl2tpd/ directory.
| root@rahul-pc~# mkdir /var/run/xl2tpd/root@rahul-pc~# ln -s /usr/local/sbin/l2tp-control /var/run/xl2tpd/l2tp-control |
Now you can start the xl2tpd tunneling server by giving the above commands. It will start & work perfectly.



3 comments:
I find layer 3 tunnelling protocol works better than layer 2. It is more reliable and more difficult to detect.
(VPN server)
You don't need to get a binary file named l2pt-control. it's more of a configuration file.
Try:
mkdir -p /var/run/xl2tpd
echo "c L2TPserver" > /var/run/xl2tpd/l2tp-control
You say no one is using L2TP VPN anymore... what are people using for linux vpn server instead ???
Post a Comment